Bitlocker Without Tpm Windows Server 2008 R2
Without the TPM, a USB startup key or startup password is necessary for the server at every boot. For this tutorial, the server also needs to be domain-joined because we need a way to back up the BitLocker recovery keys if the server runs into trouble and needs those keys. Enabling BitLocker on Server 2008 R2. I've enabled the feature in Server Manager, rebooted, and let the wizard finish the feature installation. However when I click on the data drive to turn on BitLocker under the Control Panel - BitLocker Drive Encryption, I'm prompted to elevate my credentials then nothing happens. There is no wizard, no additional windows, etc.
In the first part of this guide you will learn how to install the BitLocker Drive Encryption feature on a Windows Server 2012 R2. Log on to Example-Server01.; On the Start screen click Server Manager.; On the Server Manager window, click Manage on the top right and from the menu select Add Roles and Features.; On the Before you begin page, click Next.; On the Select installation type page. Caution To configure Group Policy objects to backup TPM and BitLocker information in AD DS at least one of the domain controllers in your forest must be running Windows Server 2008 R2 or Windows Server 2012.If Active Directory backup of the TPM owner authorization value is enabled in an environment without the required schema extensions, the TPM.
Microsoft presented BitLocker Push Encryption (BDE), ór BitLocker, in Home windows Machine 2008 and Home windows Vista. BitLocker provides volume-level data encryption for data saved on Home windows customers and machines and defends the information when systems are offline (i.age., when the Operating-system is close down). BitLocker can prevent data breaches such as the robbery of private corporate information on worker laptop computers. In previous Windows variations this security wasn't possible without a third-party item.BitLocker can furthermore provide an integrity-checking system that makes the OS itself even more strong in the encounter of attacks. When BitLocker can be used to the program quantity, it can offer a file-integrity examining function that instantly analyzes the status of boot files like as the BIOS, Professional Boot Information (MBRs), and the NTFS boot field when the program shoes and before the Operating-system starts. If a hacker inserts harmful program code into one of the shoe files or changes one of the documents, BitLocker will identify it and obstruct the Operating-system from starting.The first version of BitLocker got some shortcomings that Microsoft addressed in the newer Operating-system produces.
In the preliminary release, only a one volume-the Operating-system drive-could be BitLocker shielded. In Machine 2008 and Vista SP1, Microsoft added assistance for BitLocker security of various volumes, including local information quantities.
In Server 2008 R2 and Home windows 7, Microsoft added BitLocker assistance for removable data memory sticks (elizabeth.g., storage sticks, external data pushes). This function is known as BitLocker To Proceed. For an overview of the disc configurations that BitLocker supports, observe Microsoft's i9000 Machine 2008 Ur2 and Windows 7 also come with an prolonged place of BitLocker Group Policy Item (GPO) configuration settings, including a brand-new data recovery agent function that allows centralized recuperation of the BitLocker-protected data in an Energetic Website directory (AD) forest.In this post I explain how you can power BitLocker without making use of a Reliable Platform Module (TPM).
A TPM is a special security chip that's constructed in to most of today's Personal computer motherboards. Making use of BitLocker with a TPM adds security value, but it also adds setup and management complexity and overhead. In inclusion, many agencies still have older computer systems that don'testosterone levels have got TPMs. You can't include a TPM to a pc; it'h either part of the system's design, or it isn't.Fortunately, Microsoft included several settings options in BitLocker that make it functional on systems that put on't have a TPM. I'll stroll you through the measures to obtain BitLocker up and running on a pc that doesn't have a TPM, I'll describe which equipment you need rather, and I'll protect best procedures you can stick to.Safeguarding the OS Commute Without a TPMBitLocker is definitely accessible in all Server 2008 R2 and Machine 2008 versions (except the Itanium edition); Windows 7 Ultimate and Enterprise; and Vista. On Home windows 7 and Vista the BitLocker logic is set up as part of the Operating-system installation procedure.
On Server 2008 R2 and Machine 2008, BitLocker is certainly an optional feature that you must install. You can do so making use of the Add features choice that'h available from the Initial Configuration Duties home window or-after installation-from Server Manager.You can use BitLocker without á TPM for safeguarding your Operating-system get and for protecting fixed or removable data turns.
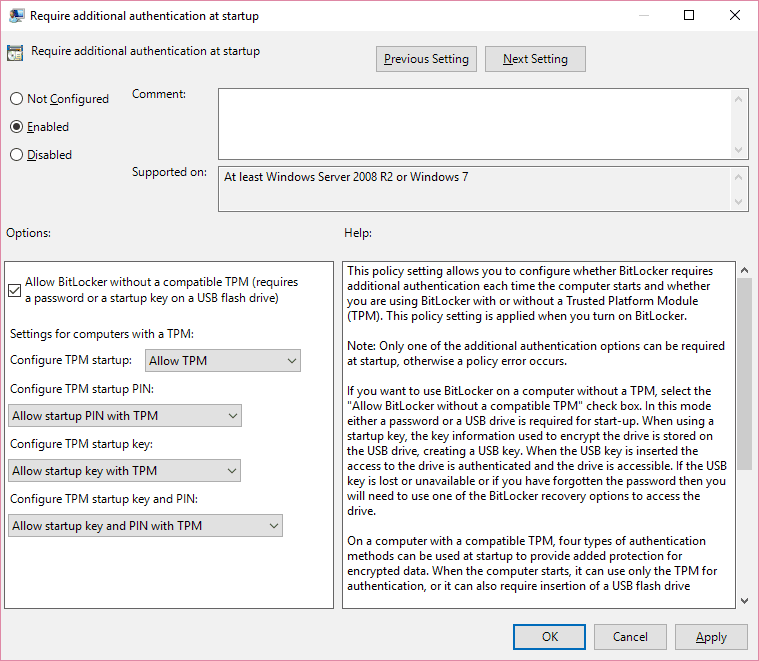
Using BitLocker without á TPM to guard OS memory sticks requires a BitLocker setup procedure that's somewhat different from the standard procedure that I describe afterwards in the write-up; it furthermore demands an additional GPO tweak that you must make prior to beginning the BitLocker setup procedure.To secure your Operating-system drive with BitLocker in the lack of a TPM, you need a detachable USB memory device and a pc outfitted with a BI0S that can boot from that device. This necessity is necessary because the USB travel holding the BitLocker encryption essential must be connected and readable thróugh the BIOS whén your program starts. The consumer must after that put in the USB push during startup to uncover the encrypted OS push.Before you can make use of BitLocker on your OS generate without á TPM, yóu must alter the default habits of the BitLocker Travel Encryption wizard. If your program doesn'testosterone levels possess á TPM, if yóur TPM can be disabled, or if your TPM is fixed in the BIOS to end up being concealed in the OS, the BitLocker Commute Encryption sorcerer will display the mistake message shown in Amount 1 during the initialization stage. The sorcerer then also pushes you to get away from the BitLocker setup-the End button is definitely the only choice.A GPO setting lets you alter this default habits. (Managers can make use of a domain-baséd GPO to internationally modify the setting.) To alter the conduct of the BitLocker Get Encryption wizard on your Server 2008 L2 or Windows 7 device, start Group Policy Manager (GPE). Click Start, Work, kind gpedit.msc, and press Enter.Navigate to the Personal computer ConfigurationAdministrative TemplatesWindows ComponentsBitLocker Commute EncryptionOperating System Forces GPO pot.
Double-click Require additional authentication at startup (for configuring Machine 2008 R2 or Windows 7 techniques) or Require additional authentication at startup (Home windows Machine 2008 and Windows Windows vista (for configuring Machine 2008 or Windows vista systems). Then click Enabled to enable adjustments to the policy, as Figure 2 shows.If the AIlow BitLocker without á suitable TPM choice isn'capital t selected, choose it now. Click Fine and shut GPE. Use gpupdate.exe to revise the GPO settings on your machine from the order line.After you create the GPO change, the BitLocker Get Encryption sorcerer will simply no longer create a TPM mistake during initialization. The sorcerer will provide the Require a Startup essential at every startup option as the only startup preference. When you click on this startup preference, the sorcerer will fast you to put in a removable USB memory device to conserve the startup essential.
After the BitLocker Commute Encryption sorcerer completes successfully, you'll become caused to plug in the BitLocker USB key every time your system boots.A similar GPO environment is available in Server 2008 and Windows vista. This environment is situated in the Personal computer ConfigurationAdministrative TemplatesWindows ComponentsBitLocker Travel Encryption GPO container's Handle Panel Set up: Enable Advanced Beginning Options entrance.On Server 2008 and Windows vista, you require to get ready your OS travel before you can guard it with BitLocker. BitLocker needs a special program partition to shop system documents that can't be encrypted and that are usually needed to start or recuperate the OS.
You can create this special program partition making use of the BitLocker Drive Preparation Tool. For information about the device, including guidelines for installing it, notice the Microsoft article In Server 2008 R2 and Home windows 7 this tool is integrated into the BitLocker Drive Encryption wizard.The Encryption ProcessThe BitLocker Travel Encryption wizard makes setup simple, if not really fast. The sorcerer can take a lengthy time to run-possibly several hours based on the commute size. Encrypting my 45GN data travel with BitLocker got about two hours. The great news is definitely that the encryption takes place in the history and your computer is nevertheless able to be used during this time.
However, I still recommend that you do nothing at all else on your machine until the encryption procedure is finished because your computer might operate more slowly.Before you start the BitLocker Commute Encryption sorcerer, make certain you possess a complete back-up of the data on the drive you need to guard with BitLocker. Although the sorcerer is solid, it's nevertheless feasible for something to go incorrect (e.g., a drive hardware failing).To start the BitLocker Drive Encryption sorcerer, move to the Handle Screen BitLocker Travel Encryption applet. You'll see a listing of all the obtainable volumes that can be encrypted with BitLocker (Operating-system, fixed, and removable pushes).
Download Microsoft Bitlocker Windows 10
If you see a warning message-for illustration, a warning that thére's nó TPM present-thén you must very first total the steps specified in the previous area.In the BitLocker Commute Encryption applet, select Switch on BitLocker for the drive you wish to safeguard to start the BitLocker Push Encryption wizard. You can furthermore right-click the drive image in Windows Explorer and select Switch on BitLocker to start the wizard.The BitLocker Commute Encryption sorcerer presents you with a collection of choices to uncover the drive, as shows.These options include Use a password to uncover the travel, Make use of my intelligent credit card to unlock the push, and Immediately unlock this travel on this computer.
Unless you select to immediately open the commute, you must offer a password or wise card and associated Flag when you wish to gain access to the protected data push. The choice to instantly open the push is accessible only for fixed data drives if your OS drive will be also BitLocker protected-in which condition the data drive will be automatically revealed when you record on to Windows. If you desire to make use of a smart card to uncover your travel, you need a particular certificate and personal essential on your sensible card. For information about how to acquire such a certification from an inner Certification Authority (CA) or how to generate a self-signed certificate for this purpose, observe Microsoft'sThe sorcerer gives you the option to save the BitLocker recuperation security password to various places: to a USB display get, to a document, or as a printed record. The BitLocker recovery password is definitely of critical significance; it enables you restore access to your data if you overlook your unlock password or shed your unlock intelligent cards.
I suggest that you constantly save at least two duplicates of the recuperation password. If you make use of a USB get, you shouIdn't use thé get for anything else. Take note that you can use the BitLocker Travel Encryption appIet's Manage BitLockér option to create even more backups of the recovery key after the wizard is completed.At this point the wizard provides you with a display screen that requests whether you really wish to begin the encryption procedure. Click Begin Encrypting to move forward.When the encryption procedure starts, Windows shows an encryption progress club. On removable data pushes you have the option to pause and continue the encryption process (use the Temporary stop button to stop).
/are-all-verizon-iphone-6-unlocked.html. (iPhone 6 - Silver, Space Gray, & Gold)Silver (left) has a white glass front and a silver colored aluminum back, Space Gray (center) has a black glass front and a gray aluminum back, and Gold (right) has a white glass front and a gold colored aluminum back.On September 9, 2015, Apple initially discontinued the Gold color option, but it remains available on the used market as well as in 32 GB capacities sold in China and Taiwan. Unlike the iPod touch 5th Gen, though, which has an entirely flat display, the iPhone 6 glass display itself curves toward the also rounded sides for a 'completely smooth and continuous surface.' Although this display is quite sharp, it is worth noting that it is not true 'HD' (1920x1080), so Apple's 'Retina HD' branding is a bit misleading.All iPhone 6 models also use the same 5.44' x 2.64' x 0.27' largely aluminum body design with smooth, rounded edges reminiscent of Apple's earlier. Android enthusiasts might also notice that the 'embedded stripes' antenna design on the back of the iPhone 6 looks a bit like the rear antenna design on several models of the previously released series, as well.Each iPhone 6 model originally was available in three color options - Silver, 'Space' Gray, and Gold.Photo Credit: Apple, Inc.
This option is helpful if you require to get rid of the drive during encryption. The stop and job application choice isn'testosterone levels available during Operating-system or set get encryption.
Click on Near when the encryption process completes.You can conveniently discover whether a commute will be BitLocker secured by looking at its travel symbol in Windows Explorer. When a get is certainly encrypted its commute symbol is certainly protected with a locking mechanism mark.
A silver closed lock signifies that the get is locked; a grey open locking mechanism is displayed after you unlock the commute. To unlock an encrypted push, right-click it and choose Unlock Travel. The unlock display screen shows, where you can enter your unlock security password, as displays.Notice that the AutomaticaIly unlock ón this personal computer from today on option can end up being used just if your Operating-system drive is definitely also BitLocker guarded.BitLocker'h File-Integrity ChéckingUsing BitLocker with á TPM for safeguarding an Operating-system drive has advantages and drawbacks. In add-on to volume-Ievel encryption, BitLocker furthermore offers a file-integrity checking mechanism. As I mentioned earlier, this mechanism automatically analyzes the position of boot files like as the BI0S, MBRs, and thé NTFS boot industry when the system shoes or boots and before the OS begins.
If a hacker inserts malicious program code into one of the boot data files or changes one of the files, BitLocker will identify it and block the OS from beginning. BitLocker will after that enter into recovery setting, and you'll need the BitLocker recuperation password or recovery key to restore entry to the system.Despite the benefits of BitLocker's file-integrity checking system, BitLocker provides TPM set up and administration difficulty to your environment. These drawbacks shouldn't end up being underestimated in Iarge BitLocker deployments, especially from a complete cost of possession (TCO) point of watch.Improved SecurityBitLocker can include great security worth to your Windows systems for protecting OS, fixed, and removable data runs, also without a TPM. The Server 2008 Ur2 and Home windows 7 version of BitLocker compétes with third-párty encryption tools-ánd surpasses them whén it comes to incorporation with the Home windows OS and its built-in administration tools.
BitLocker ToGo Encryption for Home windows Server 2008 L2TechieBird Fast LinksBitLocker ToGo Encryption for Home windows Server 2008 L2BitLocker ToGo encryption is certainly a new feature that ships with Home windows Server 2008 L2 which provides encryption for removable forces. This is certainly a very important function for backups as it guarantees that backups are usually protected.Before making use of BitLocker ToGo, you will require to add the BitLocker function to Home windows Machine 2008 Ur2. From Machine Manager, select the server then click Add Functions from the Motion menu which will open up the Increase Features Sorcerer.
From there, go for BitLocker Drive Encryption and you will discover the regular BitLocker designed for non-removable memory sticks and uses a TPM (Trusted System Module) for encryption, and furthermore the fresh BitLocker ToGo used for detachable turns.To include BitLocker Commute Encryption from PowerShell, use the below program code from an elevated PowerShell control collection. Import-Module SérverManagerAdd-WindowsFeature BitLockerBitLocker TóGo can be handled by double-cIicking the BitLocker Travel Encryption symbol in the Control Panel.
Most of us tend to have got server shelves, which makes unauthorized bodily access for stuff like as eliminating or robbing computers a much harder task than with smaller user-type gadgets. But, since most rack support servers have hot-swappable hard pushes, it gets very simple for someone with destructive purpose to draw hard drives that could contain sensitive information.Protecting server information can also be challenging if you possess to deal with shared areas/closets where telco devices or also office items may be stored, especially if those are usually remote/satellite workplaces without a full-time IT individual on staff or where multiple people have access to the area. In these situations, you can use BitLocker to safeguard your organization's information. RequirementsAs with customer techniques, BitLocker demands a Trusted Platform Module (TPM) version 1.2 or later.
TPM version 2.0 provides some extra features, like as Connected Standby, but most servers aren'capital t heading to make use of that function. Without thé TPM, á USB startup essential or startup security password is essential for the sérver at every boot.For this guide, the server also demands to be domain-joined because we need a way to back again up the BitLocker recovery tips if the server runs into difficulty and needs those tips.For encrypting shoe volumes, you'll possess to make use of physical equipment., but it is backed for information runs. The exact same is real if you're.
Installing BitLockerBitLocker Commute Encryption is definitely not set up by default on Home windows Server. To set up it, we'll want to either make use of the GUI or operate a PowerShell command word. Using the GUIIn the Machine Manager, click on Add assignments and functions. Click on Next on thé Before You Start screen and Next again on the installation type, departing Role-based ór feature-based set up as the default. Choose your server and click Next again.
Skip Machine Tasks by clicking Next.On the Features window, click on the BitLocker Drive Encryption check out box.Install BitLocker Drive Encryption in Put Tasks and Features WizardWhen prompted, select the Include management tools (if relevant) check box and click on Add Functions.Include administration equipment for BitLocker Push EncryptionClick Next whén you're taken back to the Select Features screen. The install process will need a reboot; select Restart the destination server automatically if required and click lnstall. Accept the réboot warning by hitting Yes, and after that click on Install one final time. Using PowerShellTo install BitLocker Push Encryption making use of PowerShell, open a PowerShell windowpane with Supervisor rights and operate the using order.
Enable-BitLocker -MountPoint 'G:' -UsedSpaceOnly -RecoveryPasswordProtectorEnabling BitLockér with the EnabIe-BitLocker cmdlet ón an operating program driveIf you're also functioning with an present server that's i9000 happen to be in make use of, you can omit -UsedSpaceOnly so that all commute space on C: is usually encrypted in case any previous data can be lurking on now-unused portions of the drive. You can furthermore add -SkipHardwareTest to remove the necessary reboot for a hardware check out.
Enable BitLockér with the GUl on a set data driveTo encrypt a fixed data commute in the GUI, proceed to the Control Panel, alter the view to Huge (or Little) icons, and move to BitLocker Drive Encryption. Click Turn on BitLockér in the Fixéd Data Drives area.Convert on BitLocker using the GUI for set information drivesNext, you'll become asked how to uncover the fixed data drive. Because this is usually a server, and we put on't need to possess to sign in every time it reboots to enter a password to uncover the data drive, select Automatically unlock this travel on this personal computer and after that click Next.Immediately uncover this get on this computérNext, you'll want to choose whether you want to Encrypt used disk area just or Encrypt entire travel. If you're operating with a bránd-new server, utilized disk room will encrypt the drive must faster. If you're working with a server that has ended up in make use of, the whole drive choice is definitely the favored choice so that all room (like free space) is definitely encrypted. Click on Next after you've made your selection.Choose how much of your commute to encrypt: utilized area or whole driveOn the final screen, click on Begin encrypting to begin the encryption process.Begin encrypting Enable BitLockér with PowerShell ón a set information driveTo enable BitLockér on a fixed data drive, run the using PowerShell control. Enable-BitlockerAutoUnlock - Support 'D:'Enabling BitLockér with the EnabIe-BitLocker cmdlet ón a fixed information driveThe first PowerShell series is fairly very much the same as encrypting an operating system commute.
But your mouth doesn't want to help you out. Prevail One, The Rob The Viking, Mad Child. S and M we guaranteed, to breed the call of the wild. Rating: 4.2/5 (25 votes) S; Swollen Members; Anthrax Island Lyrics ‹ Tempation Once Again Moka Only Feat. /prevail-crack-your-mouth-feat-mad-child-lyrics.html. Prevail) Lyrics that I spit can seem unsettling. Open my mouth and let the bullets from the pistol fly I am finished with these thugs, causin' mischief guy. Enriching my livings a given, so we Mad Max Madchild, Prevail, Rob the Viking, we want rap back Diamondback, Black Mamba, Lawnmower Man. Mad Child I'm a Neanderthal, Your bound to fall, I'm wonderful We warned ya all Its foreign to y'all Its wonderful the underworld Beautiful minds, Trying to keep it independent In recruitable times. Chorus (x2) Moka We crashing through you, Now feel the magnitude Were flashing through Inside of you It has to do with how You do your thing Be true to only you.
If you're making use of a brand-néw server or á information push that has no information, you can speed up the encryption process by omitting -UsedSpaceOnly. The 2nd line allows the travel to end up being automatically unlocked when the server reboots.
Watch BitLocker recuperation passwordsIf you require to see the BitLocker recovery security passwords, you'll need to install the BitLocker Recuperation Password Viewer to make use of in Active Directory Users and Computer systems (ADUC). If you're also making use of a system that you've just encrypted making use of these directions, the audience is currently set up. You can also make use of the using PowerShell control. I totally agree with the fact!
It's one matter for someone's laptop to randomly request for a Recuperation Essential, but a sérver. In a perfect globe, you're working all your workIoads in Hypér-V and á non-booting sérver isn'testosterone levels as big of a offer than state a SQL server or Swap not arriving back up. In a ideal planet, your infrastructure would have got more than enough redundancy to deal with the outage óf a server thát won't shoe because of a BitLocker issue. As for backups, simply because long as the merchant supports protection of BitLocker-encrypted volumes (nearly all should), you should be good to move. We have got blend of computer systems within the domain name with and without BitLocker allowed. These computer systems are sitting in the same OU.We are looking at pushing out a startup screenplay gpo to disable startup fix on all computer systems.In purchase for BitLocker enabled computer systems to cease getting to use the recuperation essential at each reboot, we integrated the two cmdIets within the stártup script to disable and enable BitLocker.bcdedit / established.manage-bde -protector -diasablemanage-bde -defender -enableWe tested it.
By operating the above cmdlets, computers with BitLocker no longer asking BitLocker recuperation essential upon restart.Nevertheless, what impact / adjustments these cmdlets would bring to the computer systems that WITHOUT bitLocker enable? Does the cmdlets make registry crucial modifications / etc?What could occur for those computer systems that perform not have BitLocker enable when operate the manage-bdé xxx cmdlets?Give thanks to you for posting. We need to disables Startup Repair from appearing credited to shutdown failures (which contains intentionally pulling the power cable) / by pushing N8 key because of security cause. We have get the bcdedit /established cmdlets tested and operating.We after that arrive to realised that computers with BitLocker allowed asking BitLocker recovery essential upon restart. Therefore, we included these two cmdIets:manage-bde -defender -diasablemanage-bde -protector -enableHowever, these computers (with and without BitLocker are usually sitting on the exact same OU).Are usually you saying that by running the -disable / -allowed on computer without BitLocker, there may be unknown risks?Tyring to discover out even more details on, as I believed by running -disable / -allowed on computer without BitLocker, that computer will disregard this cmdlets (do nothing).Unlike if l ran -off / -ón after that BitLocker will become switch ON.say thanks to you for your help.
Bitlocker Without Tpm Windows Server 2008 R2 Express
I nevertheless believe you've got some some other problem if you're also having therefore many computer systems run startup maintenance that you want to deactivate it. I utilized to help an military of systems that had been all BitLocker éncrypted and I cán't thought ever getting one go into startup restoration.I'meters stating that (1) you should check it because l haven't ánd (2) you shouldn't blindly run any command against a program without carrying out a sanity check out to observe if it is definitely required. I would never run a order like that without checking out to observe if BitLocker was enabled very first and after that neglect the control if BitLocker wasn'testosterone levels allowed.